
One critical aspect of server security, especially when running PHP, is the careful management of functions that can pose serious risks if misused. PHP, being a powerful server-side scripting language, offers a plethora of functions that, if not handled with caution, can expose vulnerabilities and potentially compromise the entire web server. Disabling dangerous PHP functions is a crucial step in fortifying the server against various security threats. Here are several reasons why taking this precautionary measure is essential:
Why to Disable PHP Functions
1. Preventing Code Injection Attacks:
Certain PHP functions, such as eval(), system(), and exec(), allow the execution of arbitrary code on the server. Hackers often exploit these functions to inject malicious code into the server, leading to unauthorized access and data breaches. Disabling these functions is a preventive measure against code injection attacks, reducing the attack surface and enhancing overall server security.
2. Mitigating File System Manipulation:
Functions like unlink(), rename(), and rmdir() enable file system manipulation. Disabling these functions helps prevent unauthorized deletion, renaming, or modification of files on the server. Attackers commonly leverage file system manipulation to disrupt services, delete critical files, or gain unauthorized access to sensitive information.
3. Enhancing Database Security:
Certain PHP functions, such as exec(), system(), and shell_exec(), can be exploited to execute arbitrary commands, including those that interact with databases. Disabling these functions mitigates the risk of SQL injection attacks, a prevalent method used by attackers to manipulate databases and gain unauthorized access to sensitive data.
4. Securing Against Cross-Site Scripting (XSS):
Functions like echo() and print() are often used to output data to a web page. If not handled properly, they can become vectors for Cross-Site Scripting attacks. By disabling or carefully controlling the usage of these functions, web developers can minimize the risk of injecting malicious scripts into web pages, thereby safeguarding users against potential attacks.
5. Protecting Server Resources:
Functions like shell_exec(), system(), and passthru() can be resource-intensive, especially if misused or abused by malicious actors. Disabling these functions helps prevent scenarios where the server resources are excessively consumed, leading to denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks. This is critical for maintaining the availability and performance of the web server.
6. Compliance with Security Best Practices:
Security best practices recommend disabling unnecessary or risky functions to reduce the attack surface and potential vulnerabilities. Following these guidelines ensures that the web server aligns with established security standards and is less susceptible to exploitation.
7. Strengthening Overall Server Resilience:
Disabling dangerous PHP functions is part of a comprehensive strategy to strengthen the overall resilience of a web server. By taking a proactive approach to security, web administrators can minimize the likelihood of successful attacks and better protect sensitive data, user information, and the integrity of the server infrastructure.
Here is a complete list of those functions that you can disable on server to increase your web security:
apache_child_terminate
apache_get_modules
apache_note
apache_setenv
define_syslog_variables
disk_free_space
disk_total_space
diskfreespace
dl
escapeshellarg
escapeshellcmd
exec
extract
get_cfg_var
get_current_user
getcwd
getenv
getlastmod
getmygid
getmyinode
getmypid
getmyuid
ini_restore
ini_set
passthru
pcntl_alarm
pcntl_exec
pcntl_fork
pcntl_get_last_error
pcntl_getpriority
pcntl_setpriority
pcntl_signal
pcntl_signal_dispatch
pcntl_sigprocmask
pcntl_sigtimedwait
pcntl_sigwaitinfo
pcntl_strerrorp
pcntl_wait
pcntl_waitpid
pcntl_wexitstatus
pcntl_wifexited
pcntl_wifsignaled
pcntl_wifstopped
pcntl_wstopsig
pcntl_wtermsig
php_uname
phpinfo
popen
posix_getlogin
posix_getpwuid
posix_kill
posix_mkfifo
posix_setpgid
posix_setsid
posix_setuid
posix_ttyname
posix_uname
posixc
proc_close
proc_get_status
proc_nice
proc_open
proc_terminate
ps_aux
putenv
readlink
runkit_function_rename
shell_exec
show_source
symlink
syslog
system
For more details on these functions search it on https://php.net/
How to disable dangerous php functions on WHM server:
You can disable any of the php function by adding it manually to disable_functions inside your php.ini file or through php.ini editor inside whm panel.
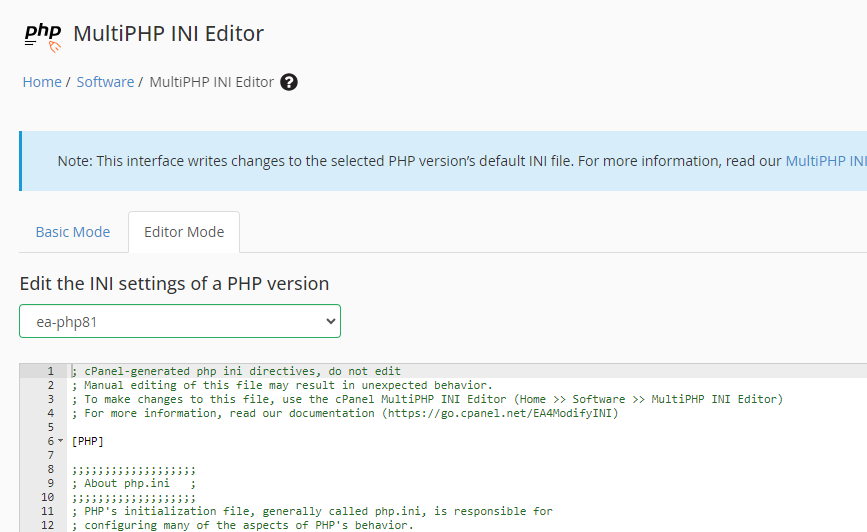
1. Log in to WHM
2. Go to Home->Software->MultiPHP INI Editor.
3. Choose the Editor Mode tab.
4. From the drop-down list choose the PHP version you want to edit.
5. In this window search for “disable_functions”.
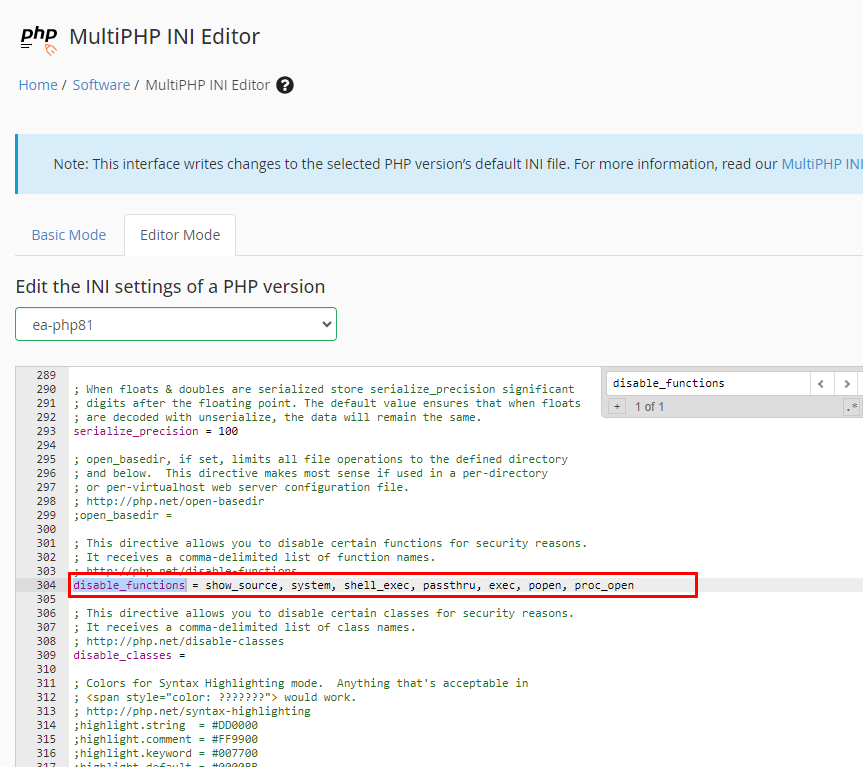
As shown in the above image write all the php functions you want to disable on your server infront of disable_functions, write all functions coma separated, then click save button.
Now if a function is disabled the user will get a warning message: phpinfo() has been disabled for security reasons